Vaccinated Atom: Cybersecurity for Nuclear Plants
Steam rises at night from the cooling towers of
the Electricite de France nuclear power station
in Dampierre-en-Burly, March 8, 2015
In
Login if you are already registered
(no votes) |
(0 votes) |
Researcher at Energy and Security Center, Eugeny Primakov Institute of World Economy and International Relations
As soon as reports came through in early 2010 about the extraordinary powers of computer viruses such as Stuxnet, which could inflict great damage to critical infrastructure, the perception of cyberthreats decisively traveled from Hollywood blockbusters into reality, overwhelming both specialists and the global public. However, five years after this incident, the international community still differs on how to convert this awareness into actions to counter these threats.
As soon as reports came through in early 2010 about the extraordinary powers of computer viruses such as Stuxnet, which could inflict great damage to critical infrastructure, the perception of cyberthreats decisively traveled from Hollywood blockbusters into reality, overwhelming both specialists and the global public. However, five years after this incident, the international community still differs on how to convert this awareness into actions to counter these threats.
In October 2015, the Royal Institute of International Affairs also known as Chatham House issued the report "Cyber Security at Civil Nuclear Facilities: Understanding the Risks" devoted to assessing relevant vulnerabilities and ways to better security. The paper is full of interesting observations focused on the belief that swift progress in developing information technologies and automating processes at all levels has generated a considerable lag in the development of cybersecurity procedures and culture, primarily in the historically secretive nuclear industry. This only gives rise to new risks and menaces.
Cybersecurity Vaccination for Nuclear Plants
Whereas the industrialized countries or those possessing the entire set of nuclear competencies are still able to develop and introduce unique and advanced information systems, the developing world is growing increasingly vulnerable because it imports nuclear technologies on a turnkey basis and is effectively tied to the process control systems attached to the equipment.
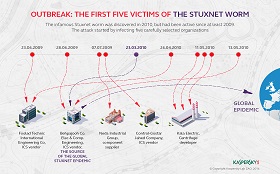
Among other things, the authors of the report come to a conclusion that the nuclear sector has become hostage to standard decisions. While previously automation at nuclear facilities was something unique or at least separate from similar arrangements by competitors, with time process control was standardized, which has enhanced the protocols for malicious programs to penetrate the systems. As such, whereas the industrialized countries or those possessing the entire set of nuclear competencies are still able to develop and introduce unique and advanced information systems, the developing world is growing increasingly vulnerable because it imports nuclear technologies on a turnkey basis and is effectively tied to the process control systems attached to the equipment. For example, Stuxnet specifically targets computers with the SCADA automated process control system [1], [2] manufactured by Siemens and used in systems for monitoring and controlling industrial, infrastructural and servicing processes at oil pipelines, electric power stations, major communication networks, airports, vessels and even military facilities all over the world. According to Kaspersky Laboratory, the makers of Stuxnet were properly trained about SCADA technologies [3]. During the investigation of effects of Stuxnet, representatives of Siemens insisted that their company had never supplied software to Iran and at the same time did not deny its presence in Bushehr. Existence of unlicensed SCADA systems in Iran has been proven by a photo provided by a global news agency that showed an expired license on a monitor at the Bushehr power plant.

Understanding the Risks
by Chatham House
The Chatham House study also questions the concept of the insularity of critical control systems and their detachment from external networks, which supposedly weaken personnel controls and inhibit the prevention of penetration. Stuxnet was delivered both through the Internet and the inter-computer transfer of data by flash disks [4]. There are even unsubstantiated theories of the targeted infection of systems at the Natanz enrichment plant and the Bushehr nuclear facility. On October 3, 2010, the Iranian authorities reported the detention of several persons who participated in an attempted cyber sabotage of the national nuclear energy program. Moreover, the report states that unregulated hookups to external networks can occur during the planned replacement of equipment components with built-in GPS and/or Wi-Fi modules, to say nothing of the situations when the connection is made directly by the contractor on the job but who later forgets to remove or disconnect the piece. The seemingly obscure channels for incursion may in fact result in the delivery of viruses to critical control elements that had been cut off from external networks for security reasons. To this end, security protocols must envisage possible remote effects of malicious software even on the detached systems.
The resolution of the cyber security conundrum for critical nuclear facilities on an industrial scale and through the self-regulation of plants, as written in the Chatham House report, may end in failure. Upon detecting malicious software, the company can instinctively conceal the fact and refrain from publicizing it and transferring over the virus to investigators in order to reduce the reputational costs, restore normal operations on their own and minimize financial risks.
The resolution of the cyber security conundrum for critical nuclear facilities on an industrial scale and through the self-regulation of plants may end in failure.
Moreover, relatively small firms lack funds for developing specialized cybersecurity systems and are settling for minimal packages that are cheap to install and support. Even major companies all over the world which are wealthy enough to allocate huge sums to cybersecurity are haunted by the absence of a security culture because of the conservatism of non-specialized personnel and overall red tape when the operation is split between several bodies and eventually loses one of the links. Even Rosatom, a state-owned corporation is not secure from human errors as far as information systems and networks are concerned. For example, in February 2012, the failure to timely pay for the rosatom.ru domain resulted in the disconnection of the company website, which remained inaccessible for 11 hours.
In Russia, this is the company Rosatom, which is responsible for the cybersecurity of national nuclear facilities through a centralized mechanism for preparing and introducing procedures for countering cyberthreats. Rosatom also appears quite able to launch such a process for improving cybersecurity standards and culture in other countries where it operates. For example, within its expansion strategy, Rosatom applies the so-called integrated offer aimed at the comprehensive development of nuclear infrastructure in its client countries, which includes the construction of the power unit, long-term fuel supplies, personnel training, preparation of the normative documentation package, legal support of the nuclear sector, as well as financial solutions mostly based on government credits. This approach generates an obvious competitive edge because Rosatom has a chain of companies in all segments of nuclear technologies and products, and can work independently, while its competitors require alliances [5].
It is still unclear what will happen if the virus directly penetrated the reactor control system.
Since cybersecurity concerns after the Stuxnet affair are on the rise, Rosatom's packaged offer should be expanded by providing specialized cybersecurity systems, for example through cooperation with Kaspersky Laboratory, Russia's leader in data protection and antivirus programs [6]. The customer would then obtain a totally secure facility, better competencies in machine building through localization, and a chance to develop its postindustrial sectors, first in systems for protecting nuclear plants with subsequent coverage of other strategic facilities.
Effects of Cyber Attacks
The report exemplifies a critical infrastructure emergency during the 1995 incident at the Ignalina Power Plant in Lithuania, which is presented as an unauthorized readiness test. Russian scientific sources tend to interpret the attack as the incursion of a local gang in revenge for a 1994 death penalty sentence imposed on one of its members. The group is thought to have used their agent within the plant personnel to alter the program for controlling nuclear fuel reloading [7]. The threat was timely revealed and neutralized by staff. In essence, this was a pure act of cyber terrorism, because information was used to harm the information system [8]. Another incident omitted by the Chatham House report took place in the Homi Bhabha Atomic Research Center, India, [9] in 1998, when the terrorists threatened to disable the reactor control system [10]. One more case described by the report involved the penetration of malicious software into the corporate network of Korea Hydro and Nuclear Power Co., resulting in the theft of drawings and technical information on two company's reactors and subsequent blackmail in exchange for not distributing information in the Internet.
The virus attack could have also been a diversion to conceal a more destructive action, i.e. the Stuxnet could have been used to cover up a more massive special operation against Iranian nuclear infrastructure.
The report exemplifies a critical infrastructure emergency during the 1995 incident at the Ignalina Power Plant in Lithuania, which is presented as an unauthorized readiness test. Russian scientific sources tend to interpret the attack as the incursion of a local gang in revenge for a 1994 death penalty sentence imposed on one of its members. The group is thought to have used their agent within the plant personnel to alter the program for controlling nuclear fuel reloading [7]. The threat was timely revealed and neutralized by staff. In essence, this was a pure act of cyber terrorism, because information was used to harm the information system [8]. Another incident omitted by the Chatham House report took place in the Homi Bhabha Atomic Research Center, India, [9] in 1998, when the terrorists threatened to disable the reactor control system [10]. One more case described by the report involved the penetration of malicious software into the corporate network of Korea Hydro and Nuclear Power Co., resulting in the theft of drawings and technical information on two company's reactors and subsequent blackmail in exchange for not distributing information in the Internet.
It is still unclear what will happen if the virus directly penetrated the reactor control system. Experts predict a failure of the active zone cooling system or some other major subsystem, which may temporarily shut down the entire plant. Of course, if signs of a cyber attack are found, testing all systems may take lots of time, even up to several months. In this regard, even an imitation virus infection of the plant systems could cause not only an emergency outage but also place lengthy delays on resuming operations, as could have been the case in Iran.
The virus attack could have also been a diversion to conceal a more destructive action, i.e. the Stuxnet could have been used to cover up a more massive special operation against Iranian nuclear infrastructure. On October 9, 2010, Tehran reported having uncovered espionage at national atomic facilities. Several workers were exposed to have collected classified information on purchases of equipment and commercial details in order to give them to foreign intelligence agencies.
Future attacks on critical infrastructure will become increasingly integrated, from nontrivial complex infrastructure of program codes to absolutely unexpected effects.
On the whole, cyber threats to nuclear facilities appear relatively new in view of methods but hardly in terms of effects. Emergency services at the plant, city or even region level are not really concerned about the origin of the threat. On August 4, 2010, a forest fire caused a heat-generated failure of the power line and current transformers of the ORU-200 open-type distribution device. As a result, the nuclear facility automation cut off the turbogenerator of the third power unit. The same happened during the flooding of power sources at the Fukushima facility by an earthquake and tsunami on March 11. 2011, or a hypothetical situation when a computer virus penetrated the automated control system of a nuclear plant and shut down the subsystems for cooling or power supply. In all these cases, responses would fit the established procedures, be it a natural or a manmade disaster or a virus attack.
As shown by the Stuxnet affair, attacks are much more dangerous for critical infrastructure when perpetrators resort to surprise methods to penetrate and impact systems. According to the report, the main result of the attack on Iranian nuclear facilities was the fact that ideas, penetration strategies and covert methods developed by a group of well financed professionals surfaced and to a certain extent inspired other members of the hacker community to search for new unique solutions in writing malicious software.
To this end, there is every reason to believe that future attacks on critical infrastructure will become increasingly integrated, from nontrivial complex infrastructure of program codes to absolutely unexpected effects. In order to obtain fissile materials like spent nuclear fuel, terrorist groups can refrain from carrying out direct armed attacks on nuclear power plants but rather attempt to break the enterprise corporate network and expose transportation logistics, alter routes and counterfeit traffic documentation, in other words to expose sensitive materials for subsequent seizure or theft. With process automation, the risks of such seemingly bizarre scenarios increase, which brings about the need for forecasting and developing countermeasures in advance.
Currently, no reliable mechanisms exist for identifying producers of malicious software or even their location.
Fighting Cyberterrorism Internationally
Threats and sabotage attempts against nuclear plants are not new. In most cases, dangers have been of an external nature and successfully handled [11]. However, the existing methods for protecting nuclear facilities, especially if the threat is internal, will hardly forestall nontraditional attacks. It is vital to adequately assess the threat of malicious software in principle. If it is real and affects international stability, we must develop an international convention to regulate cyberterrorism issues on the international level.
Currently, no reliable mechanisms exist for identifying producers of malicious software or even their location (the so-called attribution problem). The first virus to leave the limits of the digital space and disable real-life facilities may have been created by a team of top professionals with financial support and sanction of a sovereign state. According to experts, the process could have taken about six months for a group of 5-10 professionals. In addition, intelligence support must have been required to pinpoint the workers of Iranian nuclear sector and recruit them for obtaining access to the control systems. The virus may have also been tested at a special test ground imitating the systems of Natanz enrichment plant and/or an automated control system based on Siemens technologies. The test ground was likely to have been used for manufacturing identical copies of Iranian centrifuges to adapt the virus.
Many experts hurriedly ascribed Stuxnet to states with advanced information technologies, especially those directly interested in holding back Iran’s nuclear program, i.e. to Israel and the United States. Some even found a reference to the Book of Esther in Hebrew in a Stuxnet component. However, reliable evidence of Israeli involvement has still not been found. Israelis reject the state-based version, suggesting that the virus had been created by nongovernmental actors to conduct espionage or sabotage against Siemens or for academic experimentation.
However, while a loner or even a group of hackers operating on their own from a territory of a certain state can be traced and made accountable by national law (Americans manage to prosecute wrongdoers even beyond their territory), there are no mechanisms to uncover state or quasi-state actors implicated in a cyber attack.
While a loner or even a group of hackers operating on their own from a territory of a certain state can be traced and made accountable by national law there are no mechanisms to uncover state or quasi-state actors implicated in a cyber attack.
Tentative proto-mechanisms for protecting cyberspace from cyberterrorism already exist, although on the regional level, among them the European Convention on Cybercrime of 2001 that has been signed and recommended for implementation for the member countries of the Council of Europe [12]. But it has been far from effective because some countries including Russia have refused to ratify the document or even have even withdrawn on political grounds, protesting against the provisions permitting states to investigate cybercrimes in other countries without the consent of their governments, as well as because the treaty omits the notion of “cyberterrorism performed by a state actor” and articles describing the problem of virtual effects on real-life infrastructural facilities.
Russia refuses to ratify the Budapest Convention, at the same time promoting the idea of a comprehensive document. On Moscow’s initiative, in May 2010 the UN Commission on Crime and Criminal Justice established an intergovernmental group of experts to produce proposals for improving internal law on cybercrime on the global level. In September 2011 at the 66th UNGA Session, Russia, China, Tajikistan and Uzbekistan proposed for discussion a draft International Code of Conduct for Information Security [13] which is intended to enhance cooperation in countering criminal or terrorist activities through the use of information technologies. However, the idea has failed to find broad international support.
In 2011, Russia also introduced to the United Nations a draft Convention on International Information Security suggesting that states should declare the nonuse of information technologies for hostile action, aggression and threats to international security [14]. This approach perfectly fits with international law but the proposed mechanisms are purely declarative for member states and in view of the attribution problem appear suitable for stating the problem rather than developing mechanisms for threat reduction.
***
In fact, Stuxnet has marked the opening of the cyber arms race. Amateurs producing viruses for fun and cyber criminals engaged in blackmail and theft have been replaced by information warriors. As a result, with the spread of information systems in human life and pervasive automation of infrastructural facilities, including nuclear plants, cyber attacks have every chance to proliferate in increasingly greater dimensions.
In the nuclear sector, the range of cyber threats is quite broad and may include:
- Sabotage by impacting automated process control systems by altering the operation mode and disabling the facility.
- Espionage by penetrating corporate networks and stealing documents containing commercial/state secrets for ransom against their nonuse.
- An imitation cyber attack accompanied with parallel covert action against critical infrastructure.
- An act of terrorism or aggression by a state related that caused damage to the facility and the vicinity/population.
Of course, the list is limited by the level of understanding technical processes and methods to affect them by a perpetrator or a group of perpetrators, as well as by available funds and time for preparing a cyber attack. Hence, we must prepare for challenges and threats of a nontrivial nature.
To this end, the development of any comprehensive, legally binding mechanisms for countering the threat on the international level appears feasible only in the case of an unprecedented consensus of various political forces, which seems unlikely in the utterly polarized global community, although sentiments may change if an incident of Stuxnet dimensions took place that would unite all interested parties despite differences on other aspects of the global order.
Russia should now concentrate on strengthening its competencies for recognizing and neutralizing cyber attacks both on its own territory and in the countries that it cooperates with in the peaceful atomic sphere, primarily in countries where Russian companies operate as general contractors building nuclear plants and nuclear research centers, supplying nuclear fuel and performing other related jobs.
Notes
1. Automated process control system.
2. SCADA - Supervisory Control and Data Acquisition. In essence, SCADA is software of an automated process control system. For a detailed technical description of the worm dissemination, see: Sintsov Alexey. The Spy Tag: a History of Stuxnet Trojan. November 18, 2010. Hacker magazine. Issue 9/10. http://www.xakep.ru/post/53950/default.asp (in Russian).
3. K.B. Komarov, Deputy Director of Rosatom. Report "Rosatom Goes Global." Roundtable "Financing of Nuclear Power Plant Construction." Atomexpo-2014, Moscow, June 10, 2014.
41. Notably, the Kaspersky Laboratory is both a commercial enterprise and a center for researching new threats to cyber security. They described not only Stuxnet but similar malicious programs, among them Duqu, Flame, Gauss and Red October.
Fyodorova A.V. Super-Terrorism: New Challenges of the New Age. PIR-Center Proceedings: National and Global Security. №2 (20). Moscow, Prava Cheloveka Publishers, 2002. P. 64.
5. Ibid. P. 94.
6. BARC, Bhabha Atomic Research Center.
7. Fyodorova A.V. Super-Terrorism: New Challenges of the New Age. P. 103.
8. Fyodorova A.V. Super-Terrorism: New Challenges of the New Age. Pp. 60-90.
9. The European Convention on Cybercrime was signed and ratified by 47 states, 39 of them members of the Council of Europe. The document was Laos signed by such nonmembers as Canada, the United States, South Africa and Japan.
M.B. Kasenova. Basics for Transboundary Control over the Internet. Cybersecurity and Control over the Internet: Documents and Materials for Russian Regulators and Experts. Editor-in-Chief M.B. Kasenova. Compiled by O.V. Demidov, M.B. Kasenova. Moscow, Statut Publishers, 2013. P. 39. http://pircenter.org/media/content/files/12/13969745490.pdf (latest visit on October 29, 2015).
10. Ibid. P. 41.
(no votes) |
(0 votes) |